









HIPAA, or the Health Insurance Portability and Accountability Act, is a United States federal law that was passed in 1996. HIPAA defines requirements for the appropriate use and safeguarding of protected health information (PHI). This includes electronic protected health information, or ePHI. The provisions of the Health Information Technology for Economic and Clinical Health (HITECH) Act includes updates to the HIPAA regulations that further strengthen the privacy and security of PHI and ePHI.
Role-based and password protection
Encryption of all data and PHI elements
Complete audit records with full info
Encryption of all forms of interaction
Separation of system and tenant-level functions. Tenants only have access to their own resources.
Password complexity rules, password encryption and masking, and account lock-out ensure safety of user accounts.
Encryption of all data elements that are considered personal health information. Protect sensitive data. Third-party verified.
Encryption of all interactions, including voice recordings, screen recordings, email content, chat transcripts, etc.
Information about all login sessions, audit logs at system-level and tenant-level, and complete audit records.
Personal health information rendered unreadable in logs and comprehensive role-based access control.

Build strong customer relationships with powerful AI-driven omnichannel contact center software. Empower agents and boost ROI with powerful QM and AI.

Full compliance and comprehensive security features that ensure patient privacy, all while delivering seamless customer experiences.

Deliver seamless, personalized interactions to customers with AI-driven contact center software. Featuring built-in quality management and text/sentiment analysis.
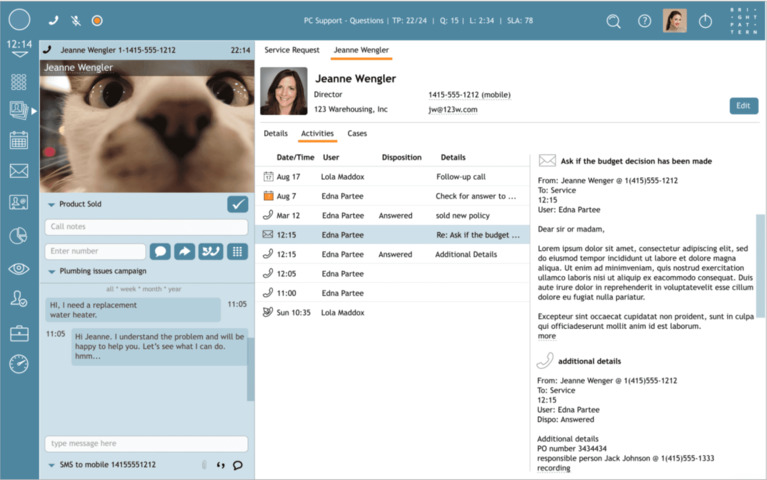
Our omnichannel contact center solution gives your organization the ability to seamlessly communicate with clients throughout their entire customer journey.
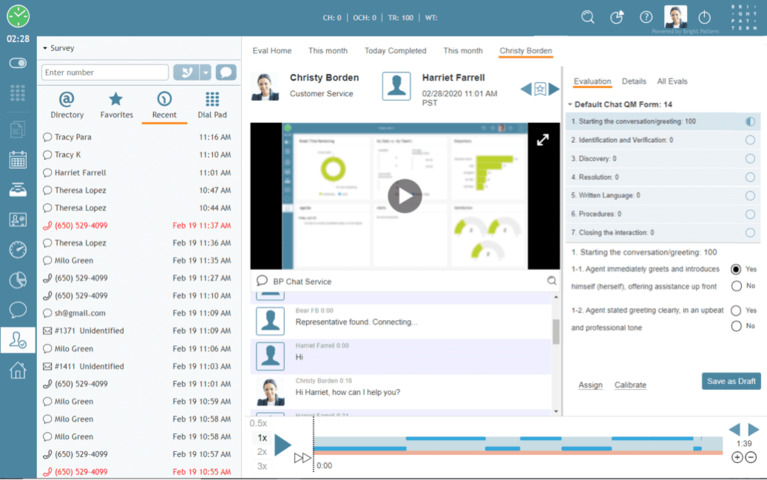
Ensure consistently excellent customer experiences and optimize call center performance with AI-powered OmniQM.
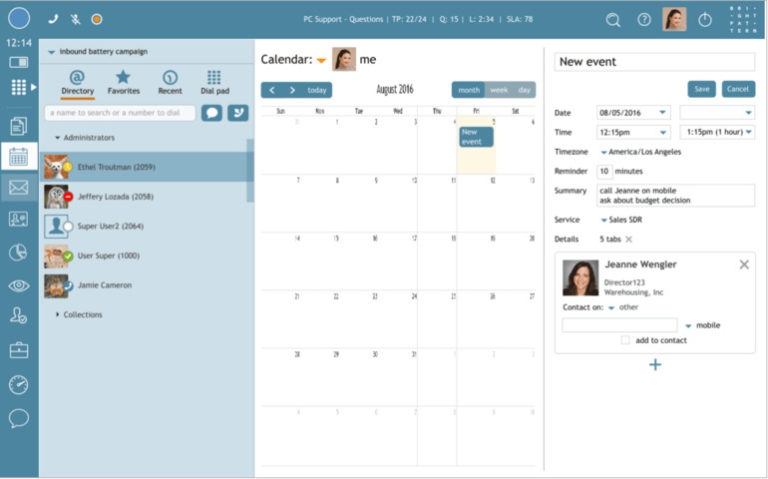
Track the customer journey with your business on any channel. Integrations with all CRM providers or your own system of records.





HIPAA regulates health insurance coverage in the United States through Title I and health information privacy and security through Title II. Furthermore, within Title II, the Privacy Rule regulates the use and disclosure of protected health information (PHI) and electronic protected information (ePHI), and the Security Rule lays out the safeguards required for HIPAA compliance. The HIPAA security rule applies to healthcare companies and their business associates and service providers.
Bright Pattern is one of the leading vendors for AI-driven omnichannel contact center software. Our contact center software is true omnichannel, allowing you to seamlessly connect with customers over any channel. Bright Pattern has the fastest ROI and the best ease-of-use in the industry.
The healthcare industry is constantly innovating due to increasing regulatory requirements and patient demands. In order to meet rising expectations, Bright Pattern provides an advanced HIPAA-compliant contact center solution that enables healthcare companies to deliver personalized customer service while protecting sensitive information and patient data.
OMNICHANNEL PATIENT EXPERIENCE
Today patients require an easy-to-use self-service IVR for simple requests, billing, and appointment scheduling, with the option to escalate the call to a live representative at any time. Allow patients to use any channel, like mobile devices, SMS, secure text, video chat, and more. Automatically and intuitively route omnichannel customer interactions to the agent best suited to solve the patient’s issue.
QUALITY MANAGEMENT
Automatically improve interaction quality in your call center with our quality management features. Bright Pattern software automatically notifies quality management coaches of conversations requiring their attention using keyword extraction and deep content analysis by IBM Watson. You can easily search both digital messages and calls for insightful content analysis.
True omnichannel is the ability to interact with clients over any channel and seamlessly switch between channels. Start a conversation with a client over the phone, then switch over to text/SMS, then switch over to email, all while maintaining the context of the conversation. Bright Pattern supports all digital channels, like SMS, text messaging, video call, voice call, email, messaging apps, and more.
Yes! Bright Pattern is fully compliant with all major laws and regulations. Bright Pattern is fully HIPAA compliant, TCPA compliant, GDPR compliant, SOC compliant, and PCI compliant. Read about our other compliances in our compliance page.
Bright Pattern’s contact center software is flexible, dynamic, and cloud-based. Bright Pattern’s contact center solution can be tailored to any industry and any situation. Request a demo and see how we can tailor Bright Pattern’s solution to your industry.